Vulnerability Management Integration Policies
Introduction
Discover the efficiency of Integration Policies for Vulnerability Management with Conviso Platform. Automate Notifications, Vulnerability Classification, and more. This powerful integration empowers your developer team to focus on critical risks, respond promptly to security concerns, and foster a culture of secure development within your organization.
Embrace Vulnerability Management with Conviso Platform's Policies Integration.
Prerequisites Ensure that you have already integrated a Defect Tracker tool or a Scanner tool with Conviso Platform. If you haven't integrated any tools yet, refer to the respective documentation on how to perform the integration.
Usage
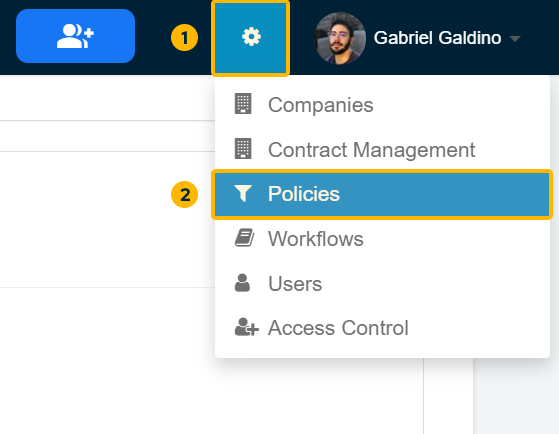
To access the Integration Policy configuration:
Click on the Gear icon (1) located in the upper-right corner.
Select "Policies" (2) from the dropdown menu.
You will be presented with the following features that ensure a more effective approach to vulnerability management, making the process more agile, consistent and secure.
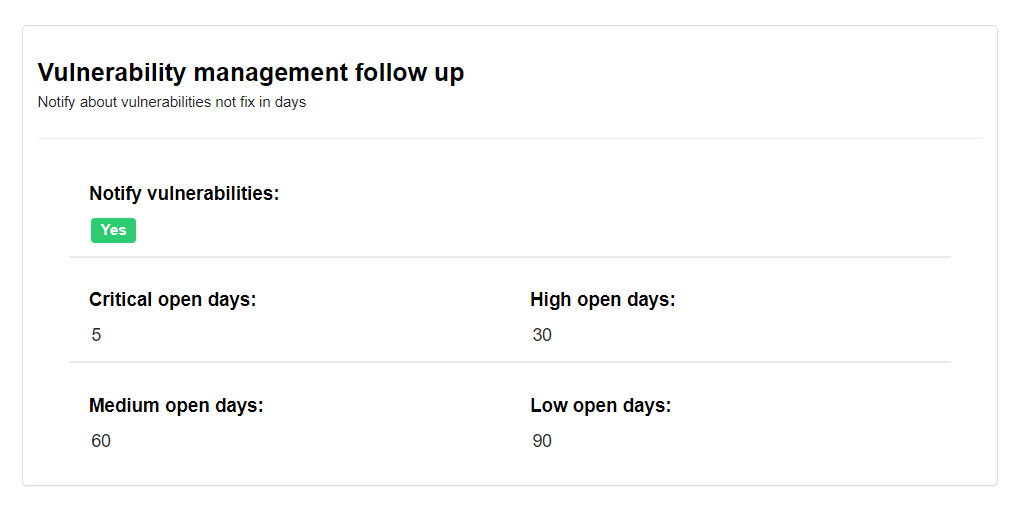
Vulnerability management follow up
This policy shows how well notifications are configured for unresolved vulnerabilities based on the number of days they remain open:
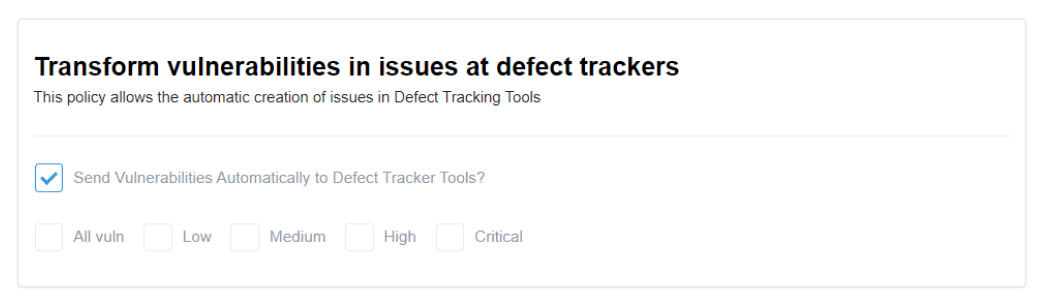
Transform vulnerabilities in issues at defect trackers
By enabling this policy, you enable the automatic creation of issues in Defect Tracking Tools for identified vulnerabilities. You can choose to send vulnerabilities automatically to the Defect Tracker Tool for all severity levels:
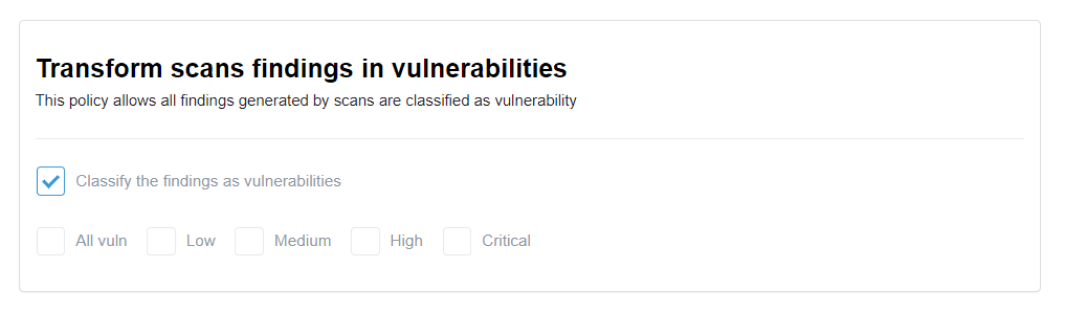
Transform scans findings in vulnerabilities
This policy streamlines the management of findings generated by scans by classifying them as vulnerabilities automatically. All findings from the scans will be treated as vulnerabilities with the specified severity levels:
Bug Bounty Score
With this feature, you have a complete view of the Bug Bounty Program score from the identified vulnerabilities.
Get in touch with our team to find out more.
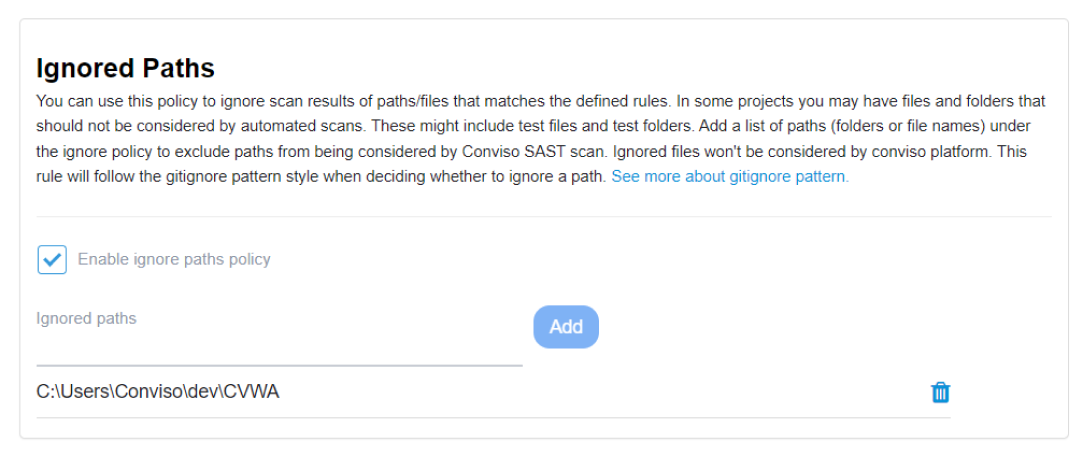
Ignored Paths
This feature empowers you to exclude specific paths or files from automated scans, enabling the omission of irrelevant files and folders during scanning, such as test files and folders. You have the flexibility to add or remove paths as needed.
After selecting your desired options, simply click the Save button to successfully integrate the policy between the Conviso Platform and your Scanner tool. Streamline your scanning process for enhanced security assessments.
Support
If you have any questions or need help using Conviso Platform, please don't hesitate to contact our support team.
Contribute to the Docs
Found something outdated or missing? Help us improve the documentation with a quick suggestion or edit.
How to contributeResources
By exploring our content, you'll find resources that will enhance your understanding of the importance of a Security Application Program.
Conviso Blog: Explore our blog, which offers a collection of articles and posts covering a wide range of AppSec topics. The content on the blog is primarily in English.
Conviso's YouTube Channel: Access a wealth of informative videos covering various topics related to AppSec. Please note that the content is primarily in Portuguese.