Creating assets with the AST
Introduction
The Conviso AST allows you to create and list assets of your company registered on the Conviso Platform.
Prerequisites
To successfully run conviso assets command you need to authenticate with the API Key.
Usage
See how to use the conviso assets command.
Listing all Assets
Use conviso assets ls [OPTIONS] to list all the Assets you have access on the Conviso Platform, execute in your terminal:
conviso assets ls --company-id $YOUR_COMPANY_ID --page "INTEGER" --limit "INTEGER"
Options
-c, --company-id
The ID of the company whose resources will be used. This option is required for all commands.
To access your company ID you need to go to settings, then "Companies", in the upper right corner next to your profile picture:
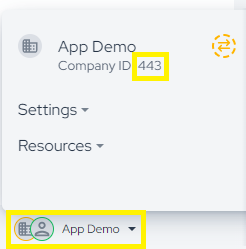
And go to your company and copy the ID number.
-p, --page
The page number to be consulted. The default value is 1.
-l, --limit
The maximum number of items per page. The default value is 32.
Example
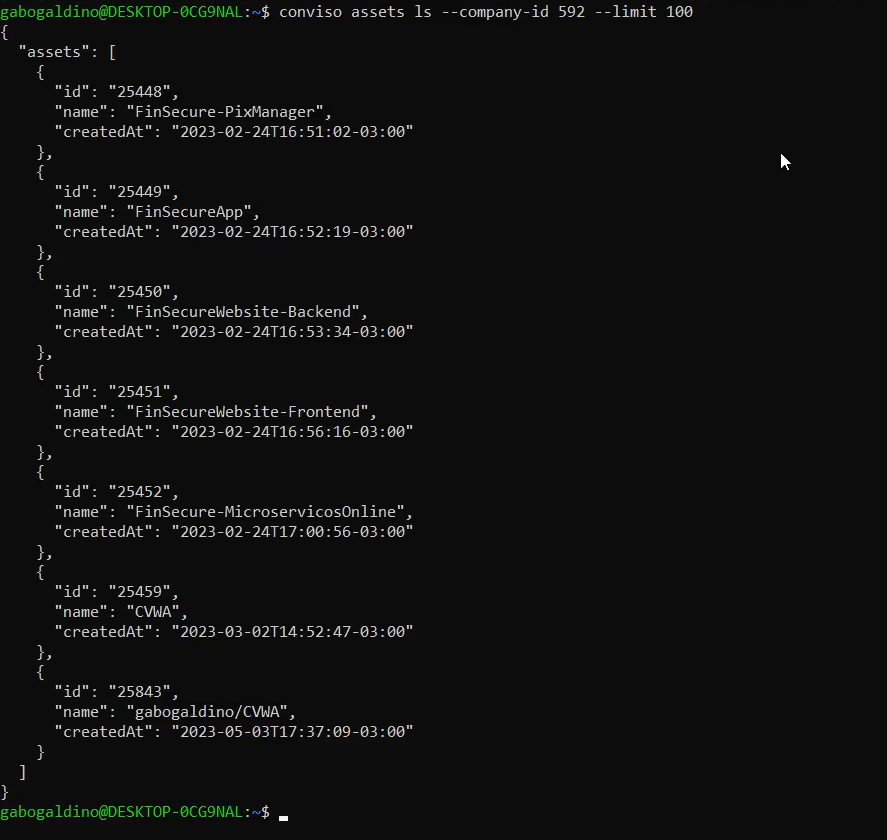
List the first 100 assets of your company:
conviso assets ls --company-id $YOUR_COMPANY_ID --limit 100
In our case this is the result that appears in the terminal:
Creating Assets
Use conviso assets create [OPTIONS] to create an asset in your company registered on the Conviso Platform.
Options
-c, --company-id
The ID of the company whose resources will be used.
-r, --repository-dir
The directory path for the asset [required]. The default value is ".".
--name
Customize the asset name.
--scan-type
Customize the asset scan type. The default value is "None".
Example
Create an asset named "asset-x" from the git repository "~/path/example":
conviso assets create --company-id $YOUR_COMPANY_ID --repository-dir "." --name "TEXT" --scan-type "TEXT"
From the moment it is created, you can access Asset Management to have asset visibility on the platform.
Support
If you have any questions or need help using our product, please don't hesitate to contact our support team.
Contribute to the Docs
Found something outdated or missing? Help us improve the documentation with a quick suggestion or edit.
How to contributeResources
By exploring our content, you'll find resources that will enhance your understanding of the importance of a Security Application Program.
Conviso Blog: Explore our blog, which offers a collection of articles and posts covering a wide range of AppSec topics. The content on the blog is primarily in English.
Conviso's YouTube Channel: Access a wealth of informative videos covering various topics related to AppSec. Please note that the content is primarily in Portuguese.