Azure Pipelines Integration
Introduction
Integrate the Conviso Platform seamlessly into your Azure DevOps Pipelines to automate and streamline your security processes. This integration ensures thorough security assessments for your applications throughout the development lifecycle.
You can run the Conviso Platform AST (Application Security Testing), which offers Static Application Security Testing (SAST), Software Composition Analysis (SCA), and Code Review directly on your Azure Pipelines.
This integration provides the CLI as a Docker image for executing tasks and establishing connections with the Conviso Platform.
Prerequisites
Before using Conviso Platform with Azure Pipelines, you must ensure that:
-
You have your Conviso API Key, a code that identifies you to Conviso Platform. Find yours using this tutorial.
-
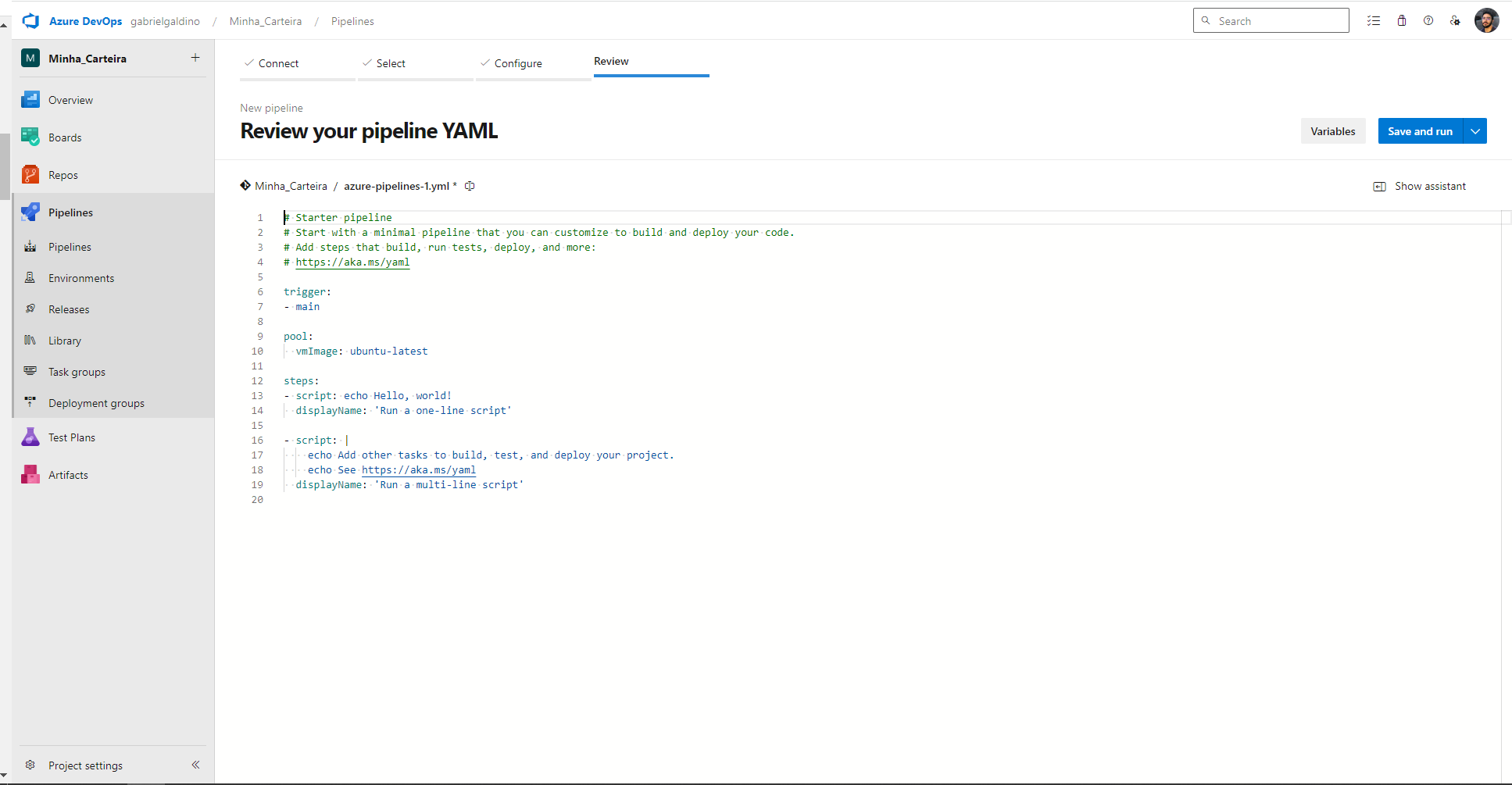
A new pipeline is created to run the automation. Follow these steps:
- Click on "Pipelines" in the left-hand menu.
- Click "New Pipeline" and configure it based on your project type.
- You will arrive at your pipeline's
YAML document.
- Set two environment variables for the runner:
CONVISO_API_KEY. To set a variable for a build pipeline:
- Go to the Pipelines page, select the relevant pipeline, and click "Edit."
- Locate the Variables section for that pipeline.
- Add or update the variable, optionally marking it as secret.
- Save the pipeline changes.
Perform a Conviso AST scan to analyze your application's security
Empower your security analysis with Application Security Testing (AST) by directly incorporating the Conviso AST scan into your pipeline. This versatile tool offers SAST, SCA, and Code Review capabilities, all integrated within your pipeline.
Follow the script below to integrate Security Code Review seamlessly into your pipeline, creating a comprehensive solution within your azure-pipelines.yml file:
trigger:
- master
jobs:
- job: Conviso_Appsec_AST
pool:
vmImage: ubuntu-latest
container:
image: 'convisoappsec/convisocli'
steps:
- checkout: self
persistCredentials: true
- bash: |
conviso ast run --vulnerability-auto-close
displayName: 'Running Conviso AST'
env:
CONVISO_API_KEY: $(CONVISO_API_KEY)
The identified vulnerabilities will be automatically sent the new Asset created on Conviso Platform.
Running the Conviso Containers
To perform the Conviso Containers, you can use the example configuration below:
trigger: none
- master
jobs:
- job: Conviso_Containers
pool:
vmImage: ubuntu-latest
container:
image: 'convisoappsec/convisocli'
steps:
- checkout: self
persistCredentials: true
- bash: |
export DOCKER_BUILDKIT=1
export IMAGE_NAME='vulnerables/web-dvwa'
export IMAGE_TAG='latest'
docker build -t $IMAGE_NAME:$IMAGE_TAG .
conviso container run "$IMAGE_NAME:$IMAGE_TAG"
displayName: 'Running Conviso AST'
env:
CONVISO_API_KEY: $(CONVISO_API_KEY)
If you'd like to scan a public image available on DockerHub, modify the configuration as shown below:
trigger: none
- master
jobs:
- job: Conviso_Containers
pool:
vmImage: ubuntu-latest
container:
image: 'convisoappsec/convisocli'
steps:
- checkout: self
persistCredentials: true
- bash: |
export IMAGE_NAME='vulnerables/web-dvwa'
export IMAGE_TAG='latest'
docker pull $IMAGE_NAME:$IMAGE_TAG
conviso container run "$IMAGE_NAME:$IMAGE_TAG"
displayName: 'Running Conviso AST'
env:
CONVISO_API_KEY: $(CONVISO_API_KEY)
These are only examples. You are required to provide the image for scanning, and you can use alternative methods based on your environment.
The IMAGE_NAME and IMAGE_TAG are variables that should be adjusted based on your project. For example, you may want to name the image after your project or version it differently.
Importing and Synchronizing Assets from External Scanners
Integrating the Conviso Platform with external scanners such as Checkmarx, Fortify, or Dependency-Track allows for automated asset import and synchronization. This ensures that your Conviso Platform remains up-to-date with the latest scan results. To configure this behavior, follow these steps:
- Access the Azure DevOps Marketplace.
- Search for Conviso Azure Sync Task or directly visit this link.
- Click on Get it free.
- Edit Your Azure DevOps Pipeline.
- Configure the Pipeline with the Following Code:
steps:
- task: convisoAzureSyncTask@1
inputs:
API_KEY: $(CONVISO_API_KEY)
PROJECT_ID: 'external-tool-project-id'
INTEGRATION: 'FORTIFY' # or 'DEPENDENCY_TRACK' or 'CHECKMARX'
COMPANY_ID: 'your-company-id'
- Save it and run the pipeline.
Field Descriptions:
- API_KEY: Your Conviso API Key, referenced as
$(CONVISO_API_KEY)in the pipeline variables. - PROJECT_ID: The project ID from the external scanner (e.g., Fortify, Checkmarx, Dependency-Track).
- INTEGRATION: The name of the integration as specified in Conviso's GraphQL schema (e.g., 'FORTIFY', 'CHECKMARX', 'DEPENDENCY_TRACK').
- COMPANY_ID: Your company ID in the Conviso Platform.
Expected Behaviors:
- Importing a New Project: If the external scanner's project does not exist in the Conviso Platform, it will be imported as a new asset.
- Synchronizing an Existing Project: If the project already exists in the Conviso Platform, it will be synchronized to update its data.
In both scenarios, the process is triggered by the pipeline and executed asynchronously. You can monitor the progress directly within the respective asset on the Conviso Platform.
Troubleshooting
If you encounter authentication issues after loading the CONVISO_API_KEY variable, please ensure it has been properly loaded within the environment session of all tasks utilizing the CLI.
Support
If you have any questions or need help using our product, please don't hesitate to contact our support team.
Resources
By exploring our content, you'll find resources to help you to understand the benefits of the Conviso Platform integrations for Secure CI/CD Pipeline:
AppSec: Integrations with CI/CD tools through Conviso Platform: Follow this article to understand how we can integrate your main tools within a single platform.
 'Azure Pipelines page for “create a new pipeline')
'Azure Pipelines page for “create a new pipeline')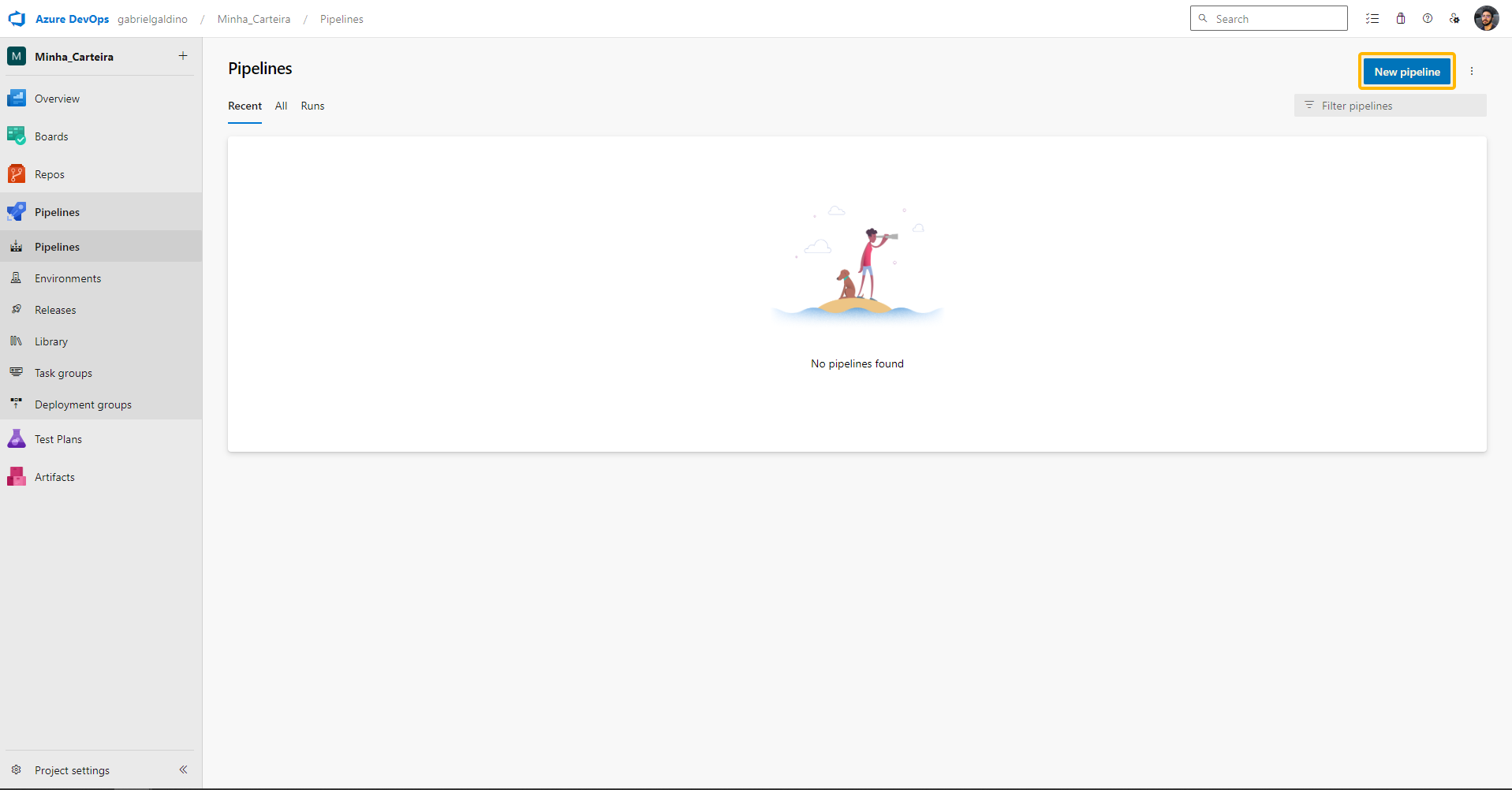 'Azure Pipelines page for "review your yaml pipeline"')
'Azure Pipelines page for "review your yaml pipeline"')