Azure Pipelines Graph Mode Integration
Introduction
Integrate the Conviso Platform seamlessly into your Azure DevOps Pipelines to automate and streamline your security processes. This integration ensures thorough security assessments for your applications throughout the development lifecycle.
The Azure Pipelines is a CI/CD module of the Azure Devops platform. Through this module, it is possible to create automation routines with various tasks that are available on Azure's marketplace. Currently, the integration with Conviso consists of Bash-type tasks. Among the tasks are: the CLI command line interface (CLI available at PyPi).
Requirements
In order for the experience with Conviso's services to be complete, it is necessary to meet all the requirements below:
-
Hosted Agent Pool (Ubuntu 22.04 or higher) with Docker installed or Agent Cloud Azure;
- External access (can be limited to Conviso's registry for AST, Dockerhub and Conviso Platform).
First Steps
Given an Azure DevOps project, to create a Welcome Pipeline you can follow the steps below:
-
At the DevOps Project root, click at Pipelines;
-
At the upper right menu, click at New Pipeline;
-
Select the Use the classic editor to create a pipeline without YAML option;
-
At Select your Repository step, select the platform where your code is hosted, the repository and the branch for pipeline execution and click at Continue;
-
Select the Start with an Empty Job option;
-
Rename the Agent Job 1 to Conviso Agent, selecting Agent Pool option as Azure Pipelines and Agent Specification option as ubuntu-latest;
-
At Conviso Agent, click at the + icon to add a new task;
-
Add a Bash type task, rename the Display Name to Run Conviso AST and modify its type to Inline;
-
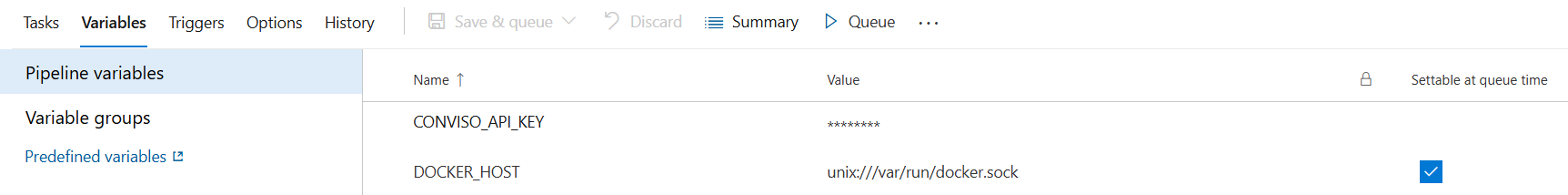
You need to define an environment variable for
CONVISO_API_KEYand set the value from Conviso Platform. It is important to set this variable as a secret. -
You will also need to define the
DOCKER_HOSTenvironment variable and set its value tounix:///var/run/docker.sock:
Running the Conviso AST
- To configure Conviso AST, within the script field, add the code snippet presented below:
docker run --rm \
-v /var/run/docker.sock:/var/run/docker.sock \
-v $(pwd):/opt/flowcli \
-e DOCKER_HOST=$(DOCKER_HOST) \
-e CONVISO_API_KEY=$(CONVISO_API_KEY) \
convisoappsec/convisocli:latest \
conviso ast run --vulnerability-auto-close
-
Click at Save & Queue. The pipeline execution will begin in a few moments.
-
The results will be sent to Conviso Platform.
Running the Conviso Containers
- To perform the Conviso Containers, you can use the example configuration below:
docker run --rm \
-v /var/run/docker.sock:/var/run/docker.sock \
-v $(pwd):/opt/flowcli \
-e DOCKER_HOST=$(DOCKER_HOST) \
-e CONVISO_API_KEY=$(CONVISO_API_KEY) \
convisoappsec/convisocli:latest \
sh -c "
export DOCKER_BUILDKIT=1 &&
export IMAGE_NAME='my-image' &&
export IMAGE_TAG='latest' &&
docker build -t \$IMAGE_NAME:\$IMAGE_TAG . &&
conviso container run \"\$IMAGE_NAME:\$IMAGE_TAG\"
"
- If you'd like to scan a public image available on DockerHub, modify the configuration as shown below:
docker run --rm \
-v /var/run/docker.sock:/var/run/docker.sock \
-v $(pwd):/opt/flowcli \
-e DOCKER_HOST=$(DOCKER_HOST) \
-e CONVISO_API_KEY=$(CONVISO_API_KEY) \
convisoappsec/convisocli:latest \
sh -c "
export IMAGE_NAME='my-image' &&
export IMAGE_TAG='latest' &&
docker pull \$IMAGE_NAME:\$IMAGE_TAG &&
conviso container run \"\$IMAGE_NAME:\$IMAGE_TAG\"
"
These are only examples. You are required to provide the image for scanning, and you can use alternative methods based on your environment.
The IMAGE_NAME and IMAGE_TAG are variables that should be adjusted based on your project. For example, you may want to name the image after your project or version it differently.
Importing and Synchronizing Assets from External Scanners
Integrating the Conviso Platform with external scanners such as Checkmarx, Fortify, or Dependency-Track allows for automated asset import and synchronization. This ensures that your Conviso Platform remains up-to-date with the latest scan results. To configure this behavior, follow these steps:
- Access the Azure DevOps Marketplace.
- Search for Conviso Azure Sync Task or directly visit this link.
- Click on Get it free.
- Edit Your Azure DevOps Pipeline.
- In the Pipelines variables section, add the
CONVISO_API_KEYvariable and set its value to your Conviso API Key. - Within the pipeline configuration, add the Conviso Azure Sync Task.
- Fill in the fields as follows:
- Conviso API Key:
$(CONVISO_API_KEY). - Project ID in the external tool: Project ID from the external scanner (e.g., Fortify, Checkmarx, Dependency_Track).
- Integration Name: Name of the integration in Conviso's GraphQL schema (e.g., Fortify, Checkmarx, Dependency_Track).
- Company ID: Company ID in Conviso Platform.
- Conviso API Key:
- Save the pipeline configuration and execute it to initiate the synchronization process.
Expected Behaviors:
- Importing a New Project: If the external scanner's project does not exist in the Conviso Platform, it will be imported as a new asset.
- Synchronizing an Existing Project: If the project already exists in the Conviso Platform, it will be synchronized to update its data.
In both scenarios, the process is triggered by the pipeline and executed asynchronously. You can monitor the progress directly within the respective asset on the Conviso Platform.
Troubleshooting
Configuring API Key
If authentication is not performed even when loading the CONVISO_API_KEY variable, make sure it is provided as environment variables for all tasks that use the CLI.
Ensuring Git is added to PATH Environment Variable
If you encounter the error below, ensure that the PATH environment variable includes C:\Program Files\Git\bin:
Unable to locate executable file: 'bash'. Please verify either the file path exists or the file can be found within a directory specified by the PATH environment variable.
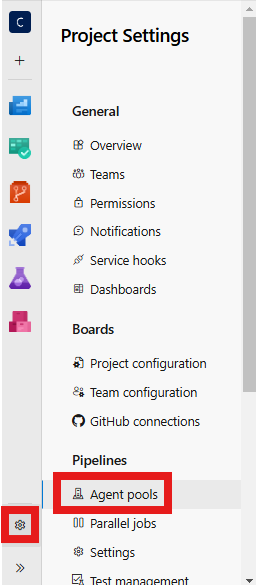
Follow these steps to verify and update it:
- Access your project in Azure;
- Navigate to Agent pools:
- In the Capabilities tab, search for the Path environment variable:
- Add
C:\Program Files\Git\binto the environment variable.
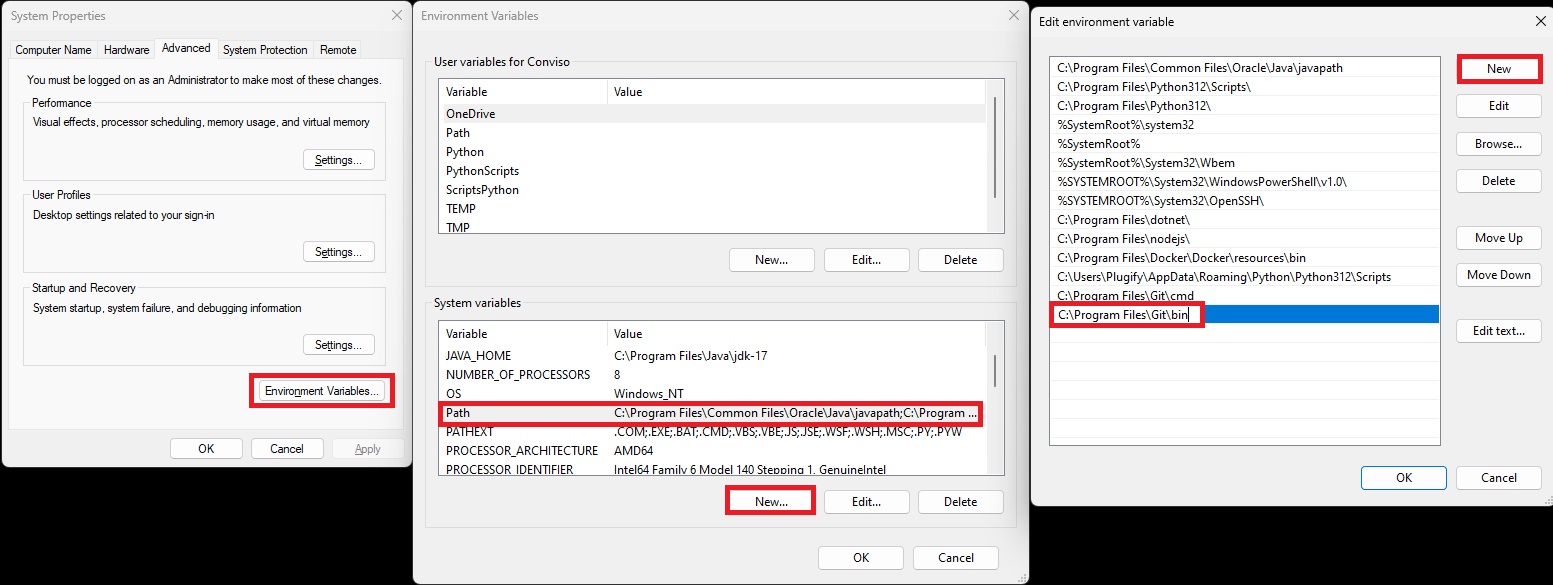
- Restart the agent service.
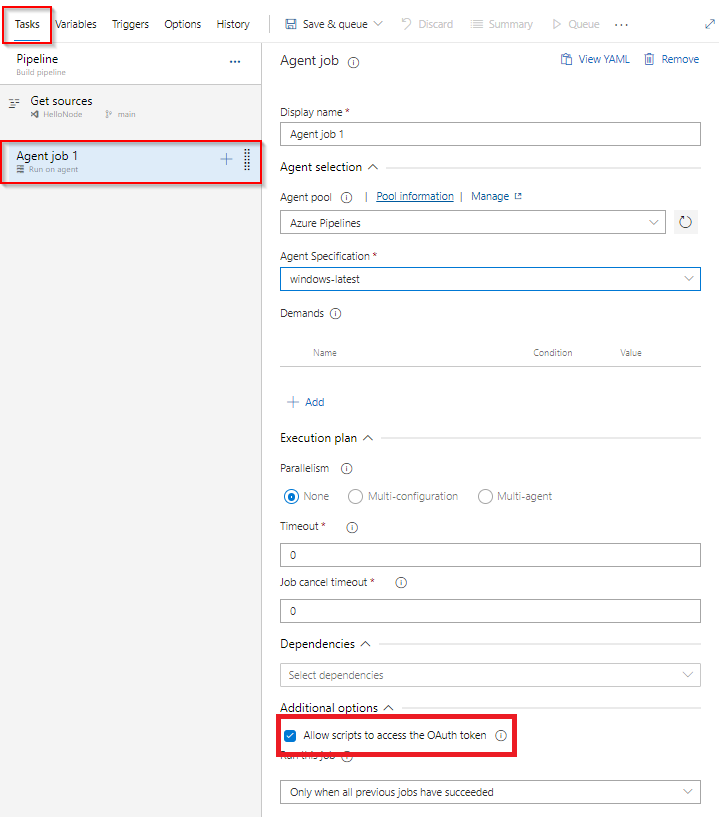
Allowing Script Access to the OAuth Token
If you encounter the following error, it indicates that the script does not have access to the OAuth token:
Error: Cmd('git') failed due to: exit code(128)
cmdline: git fetch --unshallow
stderr: 'fatal: could not read user Password for 'https://organization@dev.azure.com': terminal prompts disabled'
To resolve this issue, follow these steps:
-
Open the Agent job configuration in your pipeline settings.
-
Under Additional options, select the checkbox labeled Allow scripts to access the OAuth token:

- Save the changes and rerun the pipeline.
