Security Gate
Introduction
The Security Gate ensures that your applications meet specific security criteria before proceeding in the deployment pipeline. By defining policies based on vulnerability severity and counts, you can automatically block builds that don't meet your security standards.
The Platform allows you to configure global company-wide policies, override them with asset-specific custom rules, and monitor all Security Gate executions.
Usage
You can monitor all Security Gate runs across your company from the CI/CD > Security Gate menu.
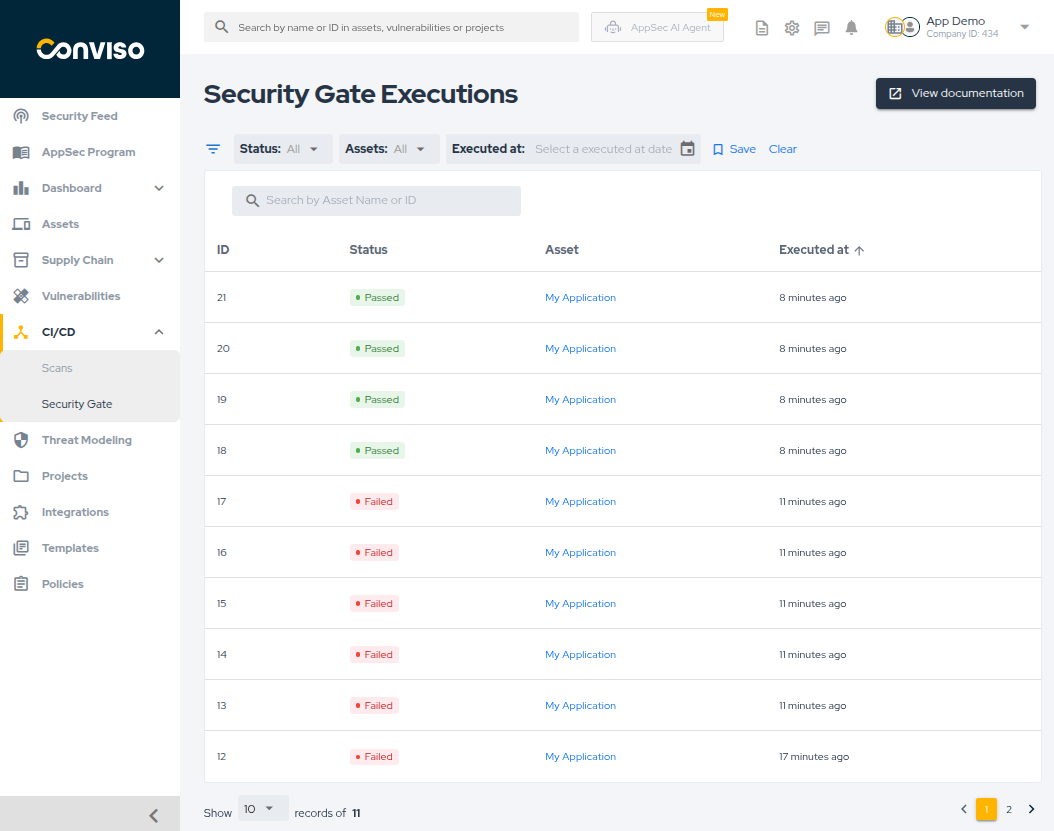
This page lists all executions, showing the Status, Asset, and Execution Date.
Features:
- Filtering: Filter by Status (Passed/Failed/Warning), Asset, or Executed at date.
- Search: Use the search bar to find executions by ID or Asset Name.
- Sorting: Sort the table by ID, Status, or Execution Date.
- Save Filter: You can save your current filter configuration to be the default view whenever you access this page.
Status Definitions:
- Passed: All vulnerability counts are within the set limits.
- Failed: At least one vulnerability has exceeded the
Max days to fixdeadline. - Warning: At least one vulnerability exceeds the
Max vulnerabilities allowedthreshold, but none have exceeded theMax days to fixlimit yet.
Execution Details
Clicking on any execution in the list opens the Execution Details page.
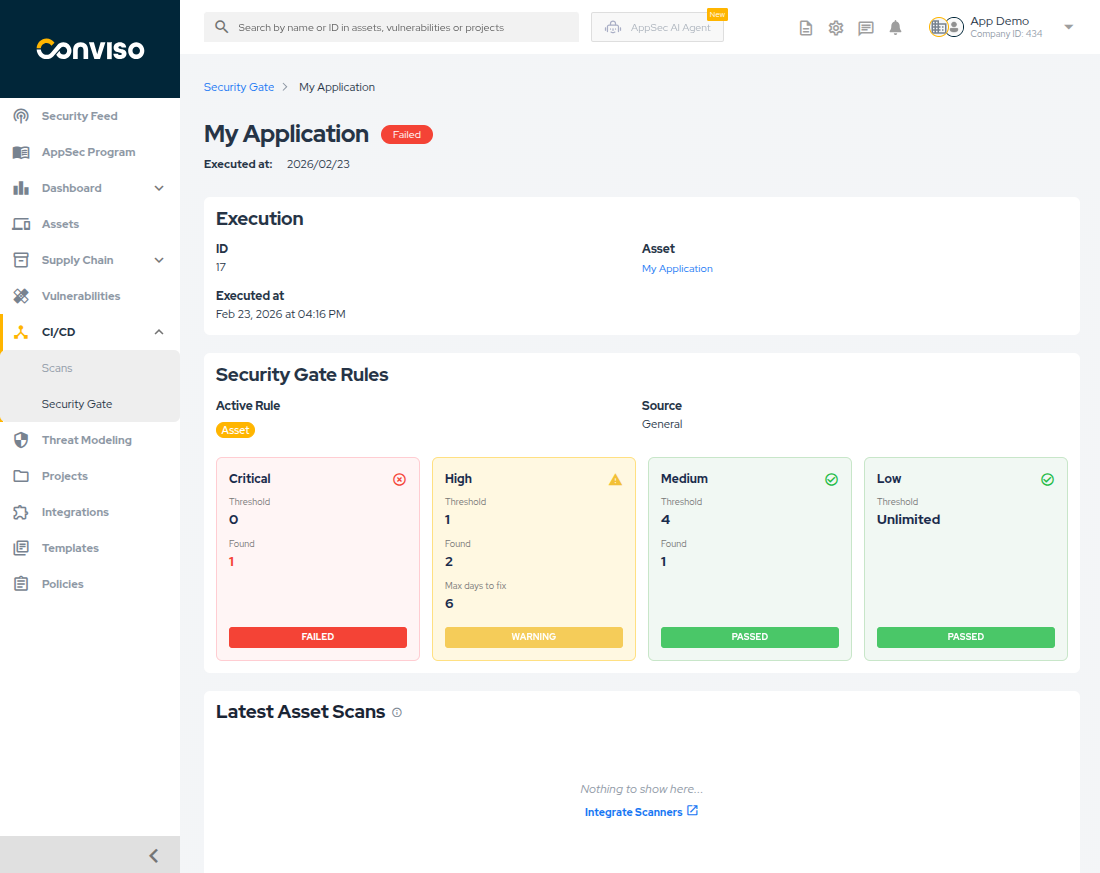
This view provides comprehensive information about why a pipeline passed or failed:
- Execution Info: ID, Asset links, and timestamp.
- Security Gate Rules: Displays the rule used and a breakdown of each severity.
- Rule Types:
- Global: Company-wide default rule applied to all assets.
- Asset: Custom rule configured per asset through the Platform.
- Custom: Rules defined directly in your repository using a YAML file or via the GraphQL API, providing an alternative for code-based configuration. You can find more information here View the YAML configuration guide and here View the GraphQL API documentation.
- It shows the Threshold (limit configured) vs. Found (actual vulnerabilities detected).
- Max days to fix: The amount of days a vulnerability can remain open before it blocks the pipeline.
- Expired: Shows the count of vulnerabilities that have already exceeded the allowed days to fix.
- Statuses like Failed (exceeded deadline or limit), Warning (exceeded limit but within deadline), or Passed (within limits) are clearly marked.
- Rule Types:
- Latest Asset Scans: A card at the bottom showing the most recent scans for this asset, providing context on where the vulnerabilities might have originated.
Configuring your Security Gate policy
Security Gate policies define the maximum number of vulnerabilities allowed by severity level. You can configure these policies in two ways through the Platform:
- Global Rule: A default rule that applies to all assets in your company.
- Asset Rules: Override the global rule for individual assets that require different thresholds.
Global Rule Configuration
The global rule serves as the default Security Gate rule for all assets. This is useful for establishing a company-wide security baseline.
- Navigate to Policies in the main menu.
- Locate the Security Gate (Global) section.
- Set the thresholds for each severity level (Critical, High, Medium, Low):
- Max Vulnerabilities Allowed:
- Click Set limit to define a maximum threshold.
- Click Unlimited to allow any number of vulnerabilities for that severity level.
- Max Days to Fix: Define the number of days a vulnerability has to be corrected before the pipeline is blocked. If this field is left blank, it is equivalent to setting it to 0, meaning there are no extra days allowed for vulnerability resolution.
- Max Vulnerabilities Allowed:
- Click Save Policies.
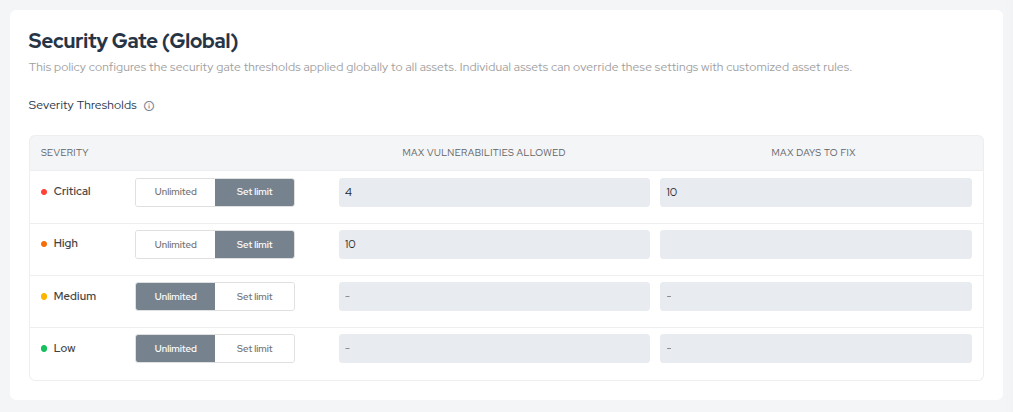
Setting limits ensures that any asset exceeding these thresholds during a pipeline scan will trigger a Security Gate result of either Warning or Failed. All assets will use these limits unless they have a custom rule configured.
Asset Rules
For specific assets that require different thresholds, you can configure custom rules that override the global rule. This is useful for:
- Legacy applications that need more lenient rules during gradual security improvements
- Critical applications that require stricter security standards
- Special projects with unique security requirements
Viewing Active Rule
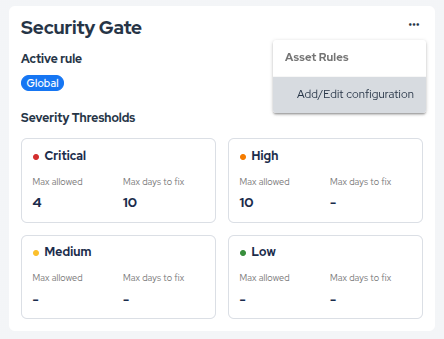
Navigate to Assets, select an asset, and go to the CI/CD tab. You will see the Security Gate card displaying which rule is currently active (Global or Asset) along with the Max allowed and Max days to fix configuration for each severity level.
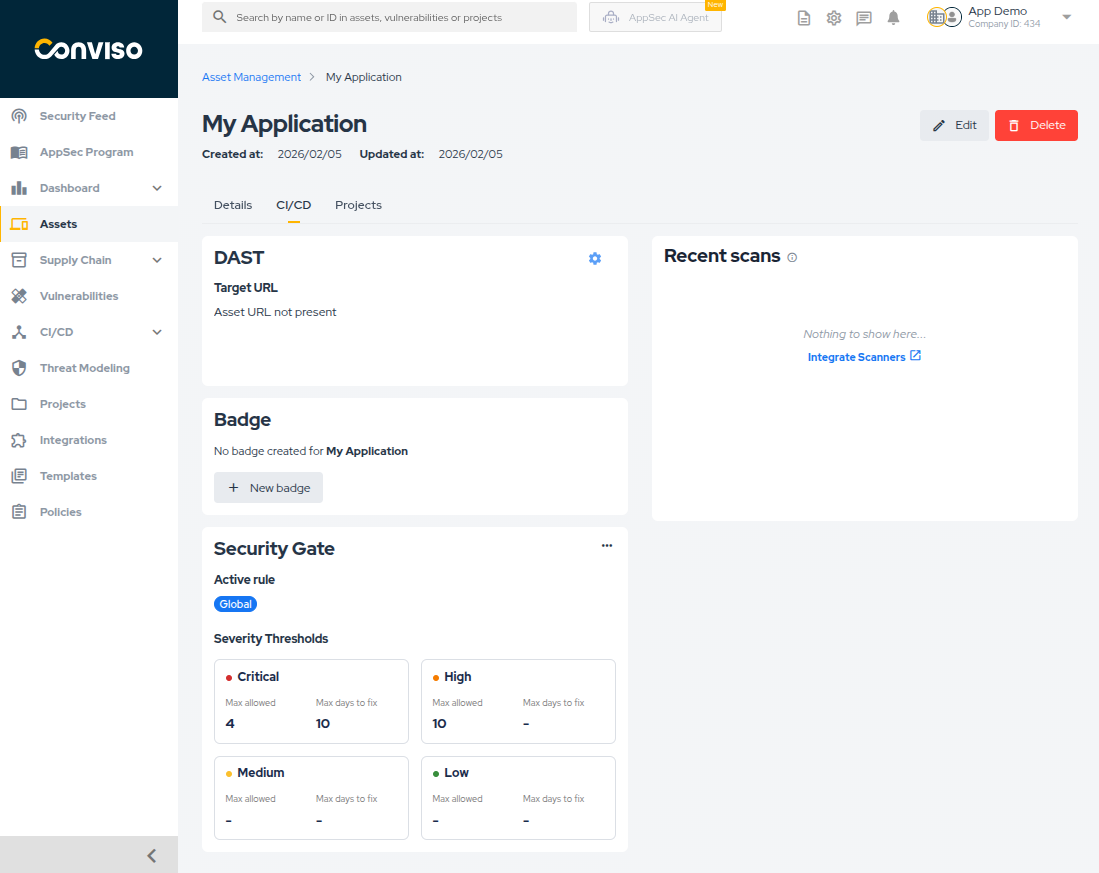
Creating an Asset Rule
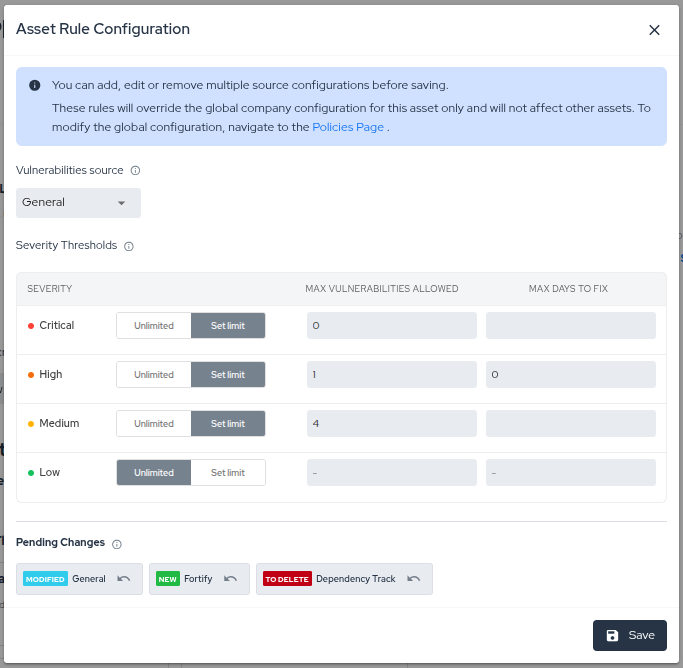
- On the Security Gate card, click the options menu (...) and select Add/Edit configuration.
- In the modal, define the specific vulnerability limits and fix deadlines for this asset.
- You can configure rules for multiple vulnerability sources (e.g., General, Sonarqube, Dependency Track) in a single session.
- Review your changes in the Pending Changes section at the bottom of the modal.
- You can Undo any specific change before saving.
- Click Save to apply all pending changes simultaneously.
Removing an Asset Rule
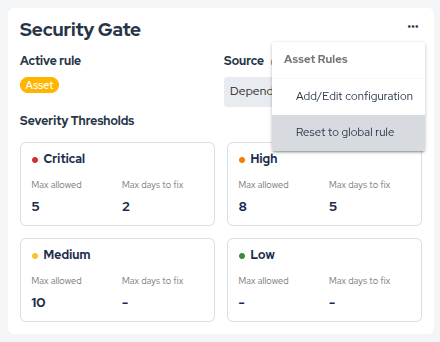
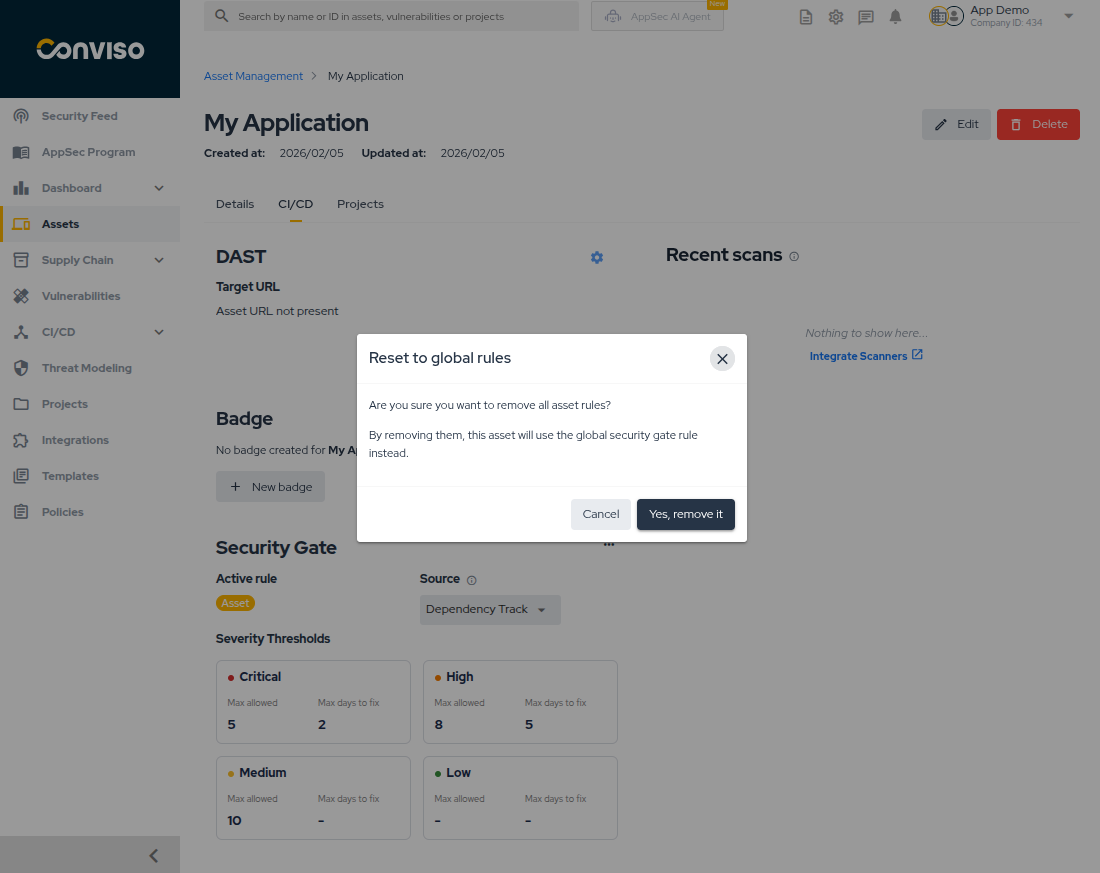
To revert an asset to the global rule:
- Click the options menu (...) on the Security Gate card.
- Select Reset to global rule.
- In the confirmation modal, click Yes, remove it to confirm.
- The asset will now use the global rule.
Running Security Gate with the AST
After configuring your policies in the Platform, integrate Security Gate into your CI/CD pipeline using the Conviso AST.
The AST will evaluate vulnerabilities against your configured policies and block the pipeline if thresholds are exceeded.
Contribute to the Docs
Found something outdated or missing? Help us improve the documentation with a quick suggestion or edit.
How to contributeResources
By exploring our content, you'll find resources that will enhance your understanding of the importance of a Security Application Program.
Conviso Blog: Explore our blog, which offers a collection of articles and posts covering a wide range of AppSec topics. The content on the blog is primarily in English.
Conviso's YouTube Channel: Access a wealth of informative videos covering various topics related to AppSec. Please note that the content is primarily in Portuguese.